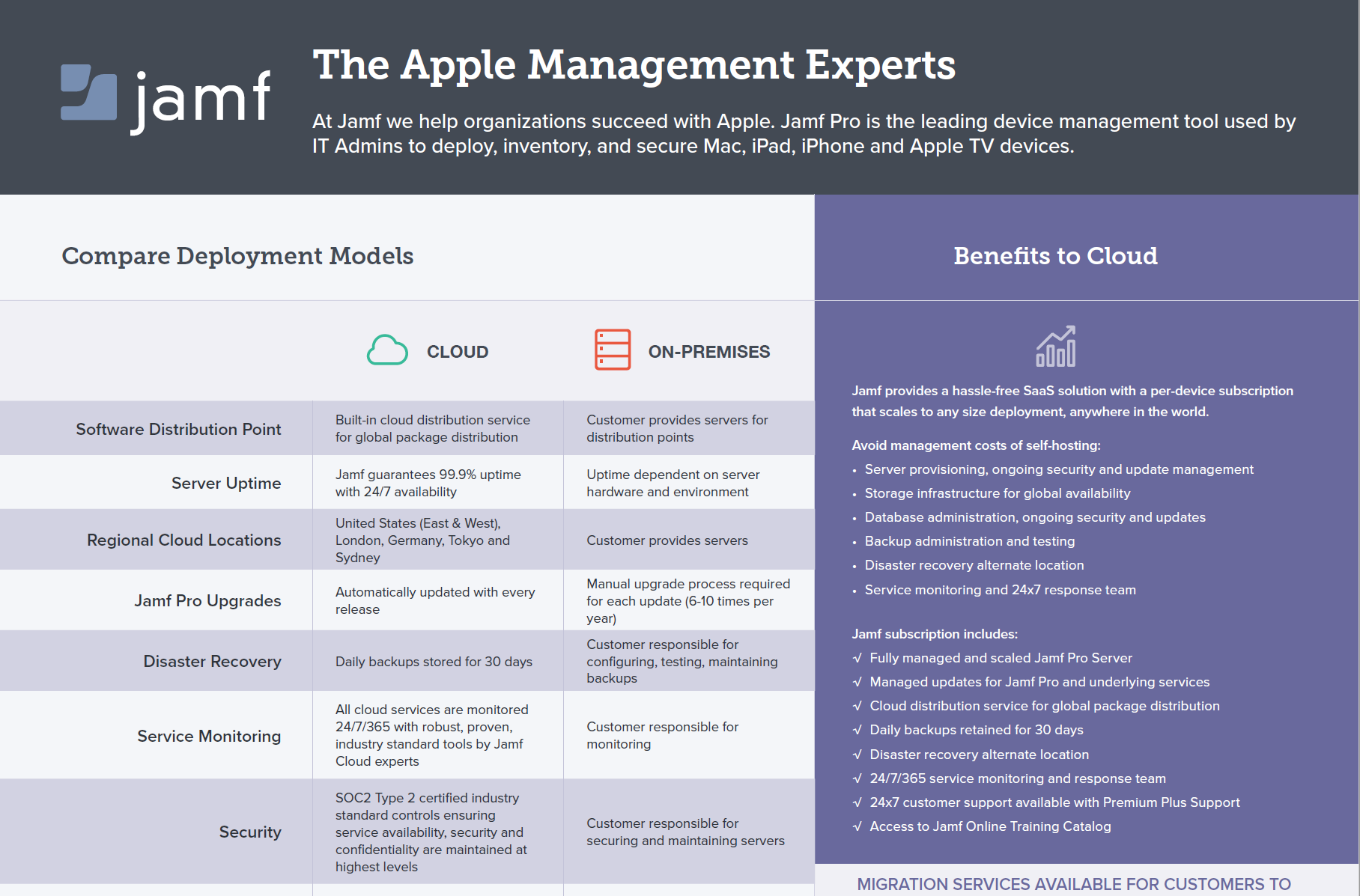
Jamf Cloud vs. On-Premises
At Jamf we help organizations succeed with Apple. Jamf Pro is the leading device management tool used by IT Admins to deploy, inventory, and secure Mac, iPad, iPhone and Apple TV devices.

At Jamf we help organizations succeed with Apple. Jamf Pro is the leading device management tool used by IT Admins to deploy, inventory, and secure Mac, iPad, iPhone and Apple TV devices.
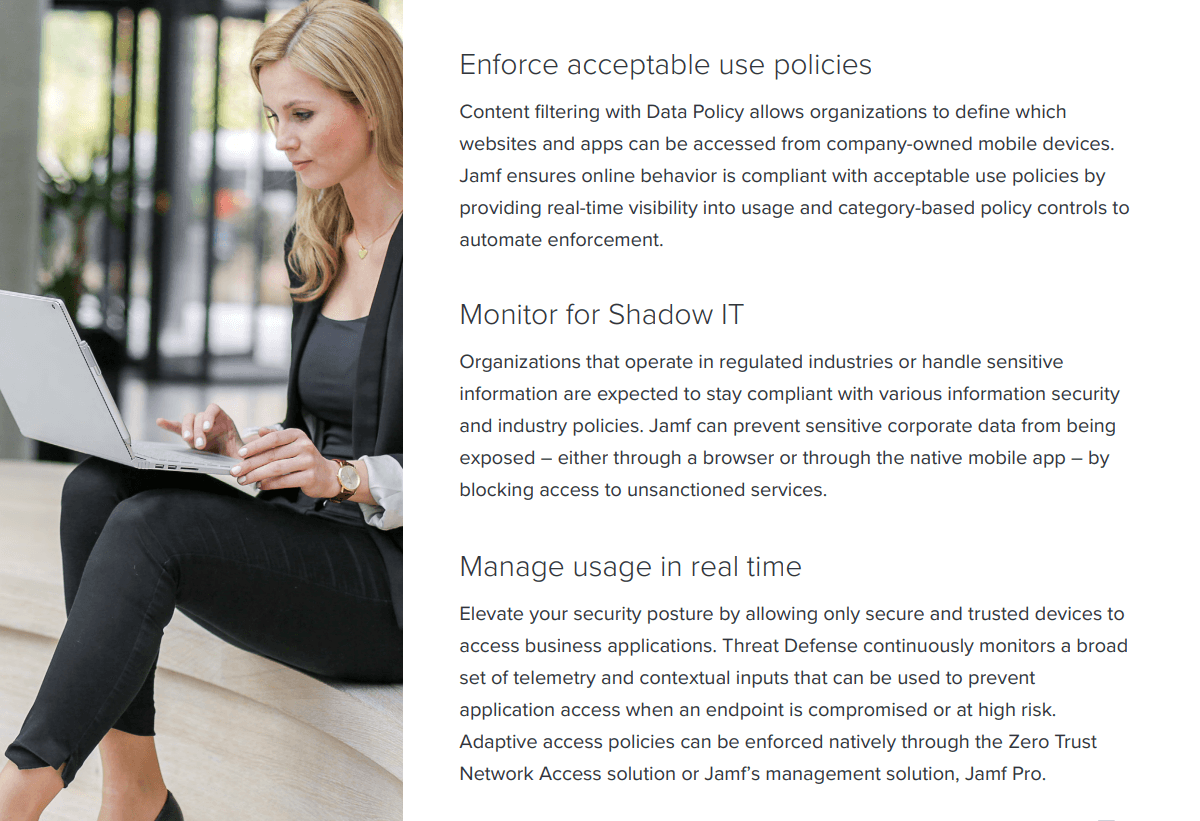
Jamf Data Policy enforce acceptable use, eliminate shadow IT, prevent excessive data usage and educate end users on their data use across cellular, roaming, and Wi-Fi networks. Enable remote work with confidence and help employees stay productive.

Jamf Threat Defense secures your mobile endpoints against compromise through threat detection and prevention of zero-day phishing and malware attacks. This is among the top concerns for all organizations, especially those that have adopted remote or hybrid environments, given the rise in targeted incidents against mobile devices from threat actors.

Jamf Threat Defense provides cloud-delivered security that operates on the device and in the network, protect your devices, users and applications from cyber threats.

Enable fast, simple and secure Zero Trust Network Access to any corporate resource. Provide teams the flexibility to work at any time and from anywhere by connecting them securely to the applications they need.

While the macOS platform has its roots in the Unix world, macOS is a unique Operating System (OS) with specific inner workings for files, processes and networks. As a result, attacks targeting macOS rarely resemble attacks against Windows or other platforms. However, most security vendors focus on building out detection, prevention and remediation capabilities for Windows first and then attempt to port the Windows-based models of their tool to Mac. Because one-size-fits-all security tooling on the market today isn’t designed for the Mac, organizations may be missing attacks on
With every Apple device, organizations need to be able to seamlessly incorporate technology that drives business initiatives by offering users secure access to the resources they need, empowering IT to deliver the functionality required in today’s modern work environment, and providing information security with the peace of mind that devices and data are protected at all times — all while delivering an exceptional experience for every employee. Jamf is the only Apple Enterprise Management solution of scale that automates the entire lifecycle of Apple in the enterprise, including
Even the most benign update may include fixes to a series of critical security flaws that an attacker could leverage against the device. Once an OS release is available, it is common for malicious attackers to analyze the updates to identify any patched vulnerabilities and then immediately create attacks against those. Attackers are well aware that not everyone updates their devices immediately; be that due to time, distractions, or the need for organizations to first ensure that the latest update works well with the rest of their software